Case Study: Hazeflow x Phala Network
How we adopted a fresh approach to an already established product and delivered value for Phala and the industry in general.
A lot of people keep asking us how exactly we work with blockchain protocols to properly explain their complex product and value proposition, so we decided to release one of our key studies to the public.
We’ve been partnering with Phala Network for multiple months and have achieved some great results. Of course, that wouldn’t be possible without the transparency that we are always aiming for and the openness from the Phala team to work together.
Beginning
At the beginning of our collaboration, we identified several things:
Phala is a complex protocol with many features and a well-thought-out mechanism design.
It has interesting features that most people, even those who are crypto-native, have never heard of.
Phala also has multiple strong value propositions for developers outside of web3.
As the most advanced protocol using Trusted Execution Environments (TEEs), some of its benefits are not widely known.
And many other things.
First and foremost, we are researchers, not marketers, so we always take a research-driven approach. The main goal is not to get a lot of general views, but to get views from people who might actually find what Phala is doing useful and helpful for their work.
Strategy
We’re obsessed with execution and getting things done. But first, we created a strategy that aligns with the main roadmap and vision of the Phala team, where the aim is not to take the spotlight, but to act in accordance with a global roadmap. The key things we wanted to do are:
Differentiate Phala from other TEE-based solutions and position it as a main competitor to AWS.
Maintain a user-friendly style while delving deeply into the technology, highlighting how specific technical details benefit the product and its users.
Position Phala as a thought leader in the TEE space. Currently, almost no one in the TEE space discusses the broader space in depth; they focus solely on their own solutions.
Phala Network is not a single solution but an ecosystem; the discussion should cover TEEs and their nuances with a deep understanding of various scenarios.
The primary goal is to establish Phala as the leader in the TEE space, not only by delivering an excellent product but also by explaining the key decisions behind its design and how the broader ecosystem will benefit from it.
Keep the discussion deep yet accessible. TEEs should appeal not only to high-profile individuals but also to a broader audience.
Besides the main points to keep in mind, we created a plan of precise topics and ideas (explained later in this writing) to ensure smooth transitions between our pieces of deep content.
Let’s go into what we created and why in more depth.
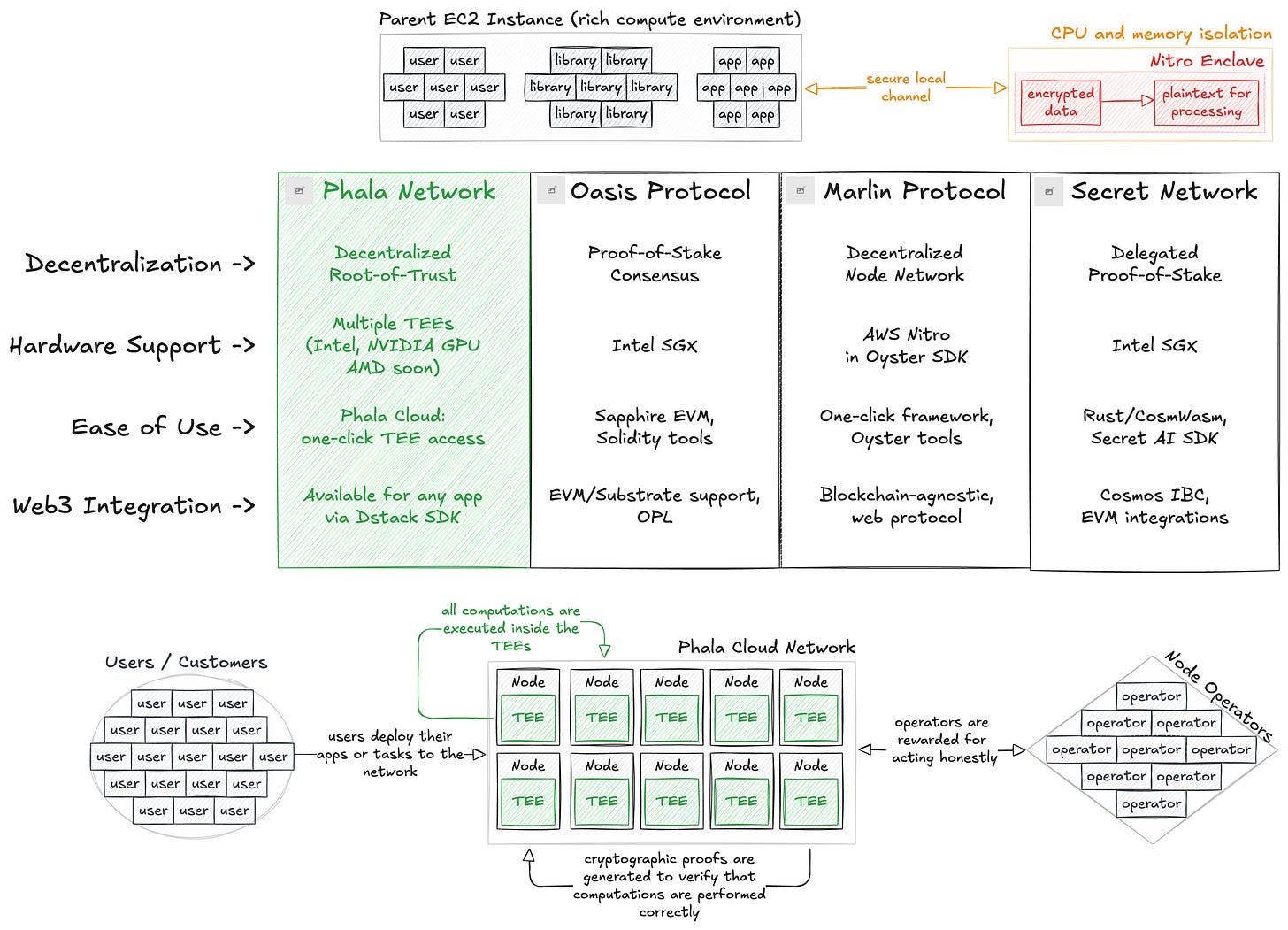
1. Phala as an improved version of AWS
We have researched and found that there is a very fast-growing demand for secure and private computing solutions, mainly because of the approximately 402 million terabytes of sensitive data generated daily.
Despite AWS holding 30% of the global cloud compute market, it still faces many challenges due to its centralized architecture, complex setup, lack of memory encryption, and limited support for decentralized applications.
We found that Phala's features directly address the downsides of AWS, so we proposed a unique approach: positioning Phala as an improved, decentralized TEE cloud that serves as a great alternative to AWS.
Therefore, we researched, wrote an article on this, and designed a few diagrams to complement it.
This piece allowed Phala to take a new, strong position and provide value to the global community by explaining the state of cloud computing.
The article is available here.
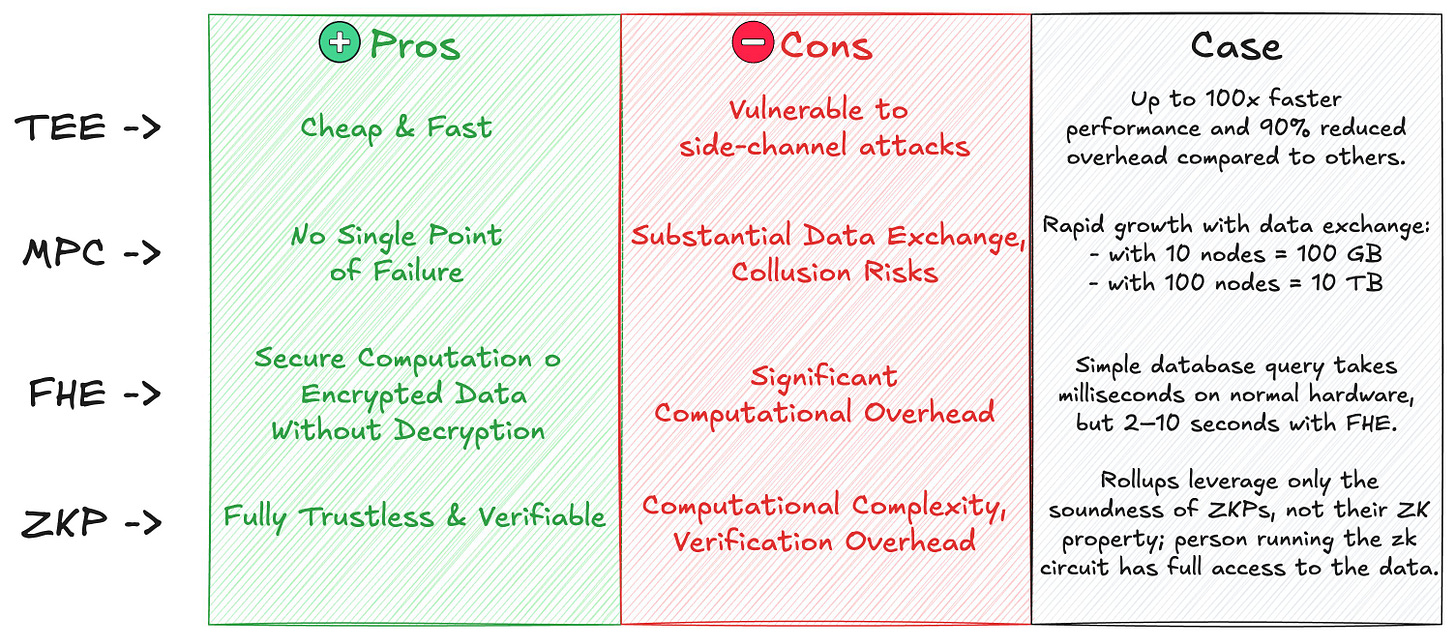
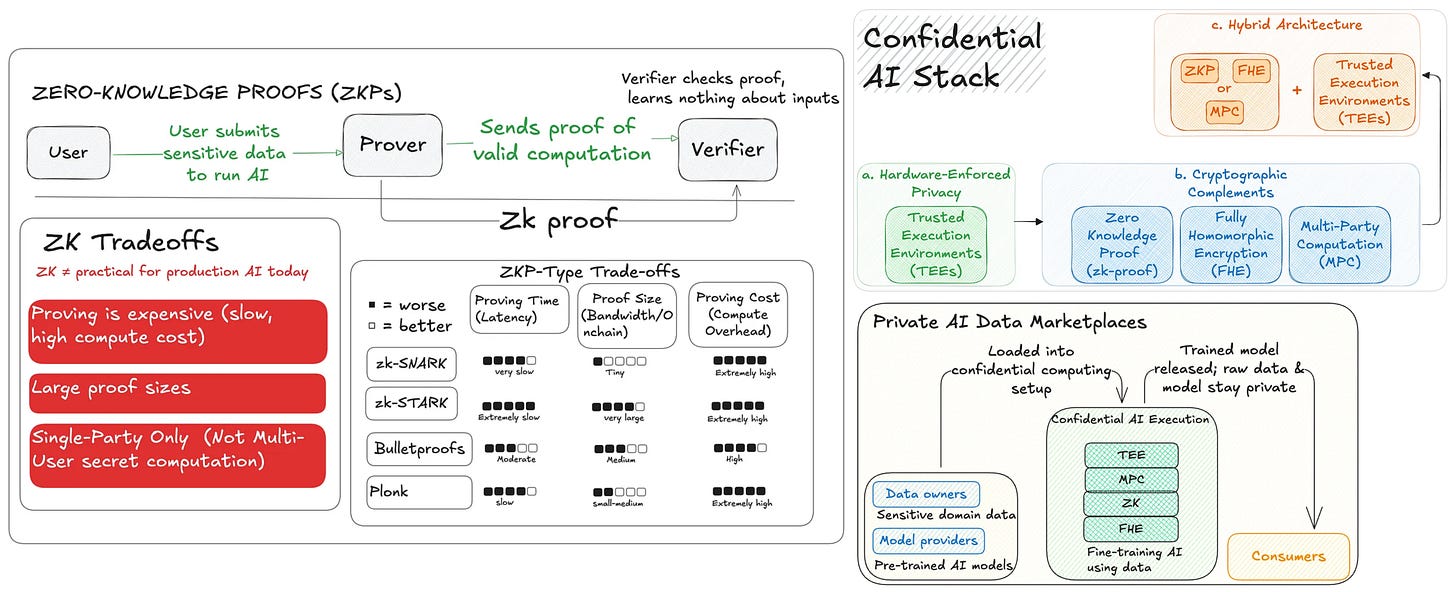
2. TEE is not competing with other encryption technologies.
There have been countless articles written comparing TEE, MPC, FHE, and ZKPs. All of these are encryption techniques, and 100% of people who have written about them have compared them, saying that TEE is better than MPC, MPC is better than FHE, and vice versa.
However, together with the Phala team, we wanted to push the narrative that these solutions are not mutually exclusive. This means you can use multiple solutions together at once: your foundation could be MPC, but you could still leverage TEE’s strengths; or your foundation could be FHE, but you could still leverage TEE, etc.
We created a long-form article that allowed Phala to take a collaborative approach with other technologies instead of competing with them. Rather than claiming to be the best, we took the approach of saying, “Everyone has their strengths that can work seamlessly together.”
There hadn't been a single article on this topic before. The article itself is available here.
3. Deep dive into GPU TEEs
Most users and ecosystem stakeholders are only aware of CPU TEEs, where computations happen inside a processor. Phala has had GPU TEEs for a long time; however, it seemed like they were hiding them. We were really shocked at how cool they are and why this hadn't been covered yet.
So, it was a no-brainer to let people know not only that GPU TEEs exist, but also to explain how they function and why they're needed. With that article, we started a shift more towards a crypto-AI theme, highlighting another of Phala’s products — Redpill.
The article is available here.
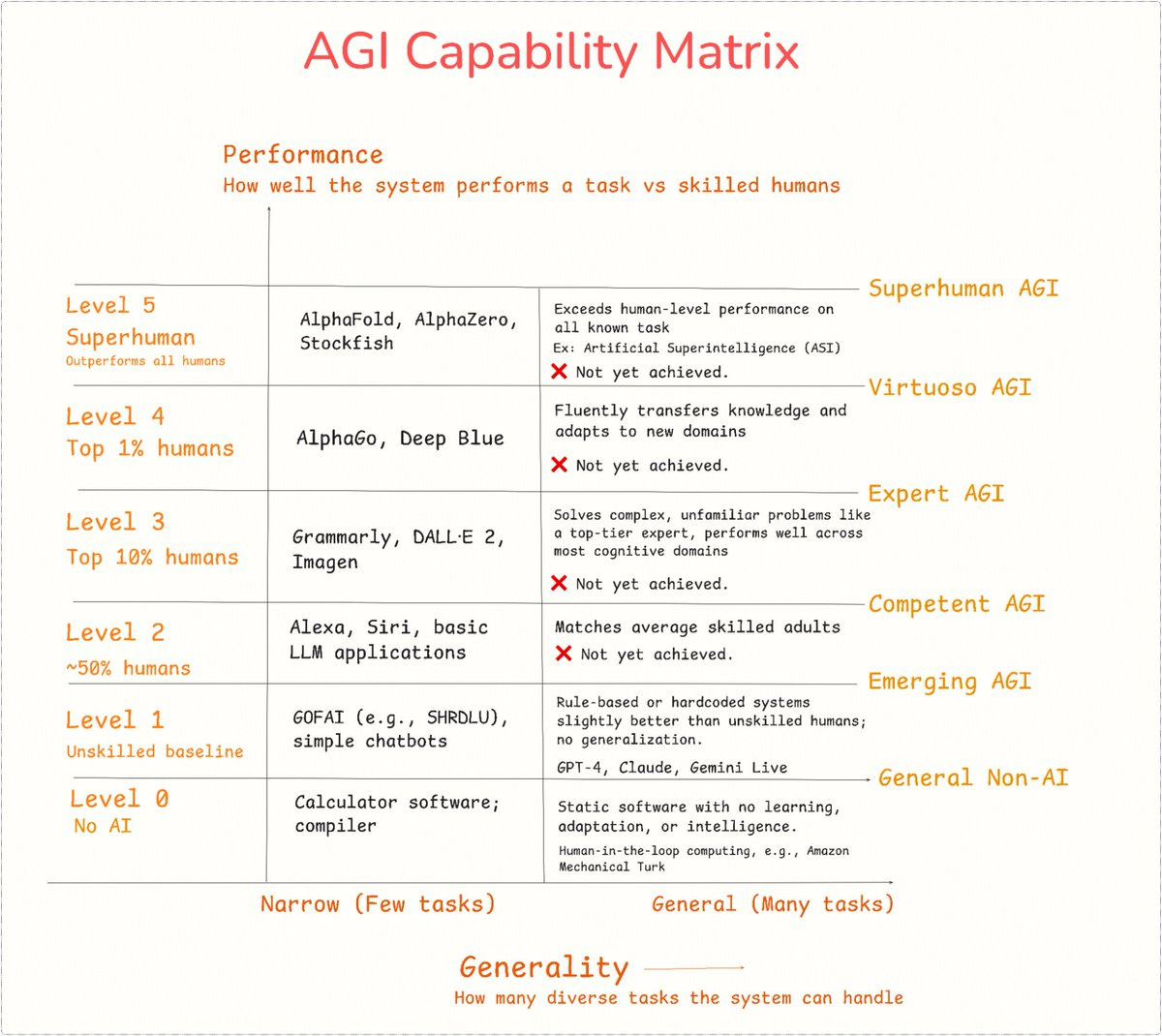
4. What Does It Take to Build Safe AGI?
Here, we discuss the need for a safe Artificial General Intelligence (AGI), emphasizing the engineering, governance, and safety infrastructure required to deploy AGI systems securely. AGI is defined as an AI capable of human-expert performance across diverse cognitive domains, with the potential to evolve into Artificial Superintelligence (ASI) through recursive self-improvement.
As we shift into AI and AGI, Phala is presented as a decentralized confidential computing platform that supports Safe AGI through its Phala Cloud, Dstack SDK, Private ML SDK, and Redpill Gateway. All of these tools enable secure, verifiable AI execution in GPU TEEs, ensuring confidentiality, integrity, and attestation for workloads like LLMs.
The article itself is available here.
5. The State of Confidential AI in 2025: Who Wins and Who Loses
We decided to release this article on our research blog, where we discuss the current landscape of confidential AI in depth, highlighting Phala’s improvements.
The article discusses the critical need for Confidential AI to secure sensitive data during processing, particularly when AI decrypts data for inference, making it vulnerable to malware, hackers, or exposure on public blockchains.
This vulnerability is especially pronounced in decentralized systems where data is replicated across nodes. We highlighted Phala as a GPU TEE cloud that combines runtime privacy with ZK/MPC proofs and was actually the first to benchmark LLM inference in secure enclaves of TEE.
The article is available here.
Moving Forward
That’s just one of the examples of how we help protocols explain their true value proposition and complex products.
We deeply believe that most things in this industry need to be simplified or properly explained. There have been countless examples of users visiting a protocol's website, blog, or technical documentation and, after 15–20 minutes of reading, still having no idea what the protocol does.
That is one of the issues we are working on, and we are proud to be doing so with Phala Network.
We are always looking to work with talented teams and long-term builders who share our research-driven approach. We are big fans of execution and always make sure that our efforts contribute to the global goal of a particular company.
Hazeflow is a blockchain research firm with experience in research, analytics, and the creation of technical, product, and educational materials.
We work with blockchain teams (especially complex-tech ones) who struggle to clearly and meaningfully explain their complex product.