How to Actually Measure the Economic Security of Blockchains? (It's Not Just About Money)
What are the parameters for measuring a blockchain's economic security beyond its total value, and what are the different security models used by various L1 blockchains?
Most people usually assume that whoever controls the majority of mining power or validator stake could manipulate or even reverse transactions, such as by double-spending, or censor new ones. However, outside of clean mathematical simulations:
How realistic is this?
What would it actually cost in the real world?
Are there other types of such attacks?
The idea of economic security is a measure of how expensive and unattractive it is for a bad actor to compromise a blockchain. It's important to distinguish this from cryptographic and smart contract security where:
Cryptographic security makes sure that the underlying technology, like digital signatures, can't be broken.
Smart contract security makes sure that the applications built on the blockchain are free of flaws that could be exploited to steal or lock up funds.
In contrast, economic security is about incentives and costs. What would it take for anyone to manipulate consensus, censor transactions, or steal value from users, assuming the cryptography is sound?
Put simply, economic security is about how value flows within a blockchain ecosystem:
If value leaks away from users to parties it was never intended for, the system has suffered an economic attack.
These leaks may happen because of a takeover (e.g. double-spends after a 51% attack), but they also happen in subtler ways: frontrunning trades, censorship-for-profit, validator cartels, or poorly designed staking systems.
Blockchains are fundamentally coordination technologies.
They allow people who don’t trust each other to interact and transact securely. And the medium of this coordination is money represented as tokens native to the system.
Every mechanism in the chain, from consensus to fee markets, is about governing how this money moves. When those mechanisms break down or are exploited, the leakage of money away from intended flows is the true cost of insecurity.
So when we ask, “How secure is Bitcoin? How secure is Ethereum? How secure are the new generation of L1s?”, we are really asking:
What does it cost to attack them?
How likely are those attacks to succeed?
And how much value could leak from users if they did?
With that in mind, let’s start with the most simple and critical measure of all: the total security budget and the cost to halt a chain.
Security Budget and the Cost to Halt Chains
Blockchains make people work for other people’s transactions and reward them in return — this creates a powerful flywheel of incentives.
The more valuable a chain becomes, the more it can spend to defend itself against attackers, and the harder it is to compromise. This protective spend is what we call the security budget. To understand it better, let’s look at the two largest blockchains: Bitcoin and Ethereum.
Bitcoin Security Budget
Bitcoin’s defense comes from miners running ASICs. Theoretically, an attacker could:
Rent hashpower. But in practice, there isn’t enough capacity available, and trying to rent it would spike costs.
Buy hardware outright. Current estimates suggest ~7 million ASICs at a cost of ~$20 billion, plus $5–22 billion annually in electricity, putting the real attack budget closer to ~$40 billion.
Even then, miners wouldn’t sell out cheaply. A successful attack would collapse Bitcoin’s value, destroying miners’ future revenue streams. Any attacker would need to compensate not just for today’s block, but for the entire future miners are giving up.
Ethereum Security Budget
Ethereum secures itself with Proof-of-Stake (PoS). An attacker can either:
Bribe validators. But validators earn steady staking rewards. To defect, they’d demand multi-year payouts far beyond a single block reward.
Stake ETH themselves. Today ~30% of ETH ($150B) is staked. To reach ⅔ majority control would require ~$280B more ETH, with the churn limit throttling entry to 1,800 validators per day.
That means months of buildup, plenty of time for defenders to react. Slashing raises the stakes: misbehaving validators can have ETH destroyed, turning attacks into acts of self-sabotage.
Rethinking the Security Budget
If our models assumed attackers could tap into infinite global markets and that all validators or miners were perfectly rational profit-seekers, then the headline security budget would be a reliable measure of safety. But real networks never meet these idealized assumptions.
Mining and staking markets are shallow, hardware and liquidity are scarce, and many participants are motivated not just by profit but also by long-term belief in the system.
Decentralization of Nodes and Validators
When validators are spread across thousands of people, different countries, and multiple software clients, it becomes much harder for anyone to coordinate an attack.
Decentralization breaks up the attack surface into many small pieces, instead of paying off or overpowering one group, an attacker has to deal with a whole network of independent actors.
In practice, this means the true cost of an attack is not just the headline security budget, but also the difficulty of persuading, bribing, or overpowering such a diverse set of participants.
Now let’s move on to how different types of economic attacks work.
Beyond Security Budgets: How Attacks Really Work
Real networks aren’t neat mathematical models. Liquidity is shallow, hardware is scarce, and many participants are motivated by belief, not just profit. Security budgets alone don’t tell the full story.
These kind of attacks fall into three broad categories:
Full-Chain Attacks (Majority Control)
Partial-Chain Attacks (Partial Control)
Ordering-Layer Attacks (MEV & Censorship)
Full-Chain Attacks (Majority Control)
In Ethereum:
With ≥33% control, an attacker can prevent a transaction from ever being finalized. This allows them to rewrite recent transaction history, reverse transfers, or cause long delays that disrupt exchanges and other services.
With ≥66% control, an attacker can finalize invalid states, like approving fake transactions. They can also permanently censor transactions, effectively blocking specific users or applications from using the blockchain.
Partial-Chain Attacks (Partial Control)
Small groups of validators can exploit the system to disrupt reliability. Even just a few nodes can stall transactions, delay cross-chain withdrawals, or force applications to pause. These attacks have a real impact on users even if the attackers don't have majority control.
Under-activity (withholding votes). Validators are supposed to vote on blocks so the network can “finalize” them. If too many validators go silent, either intentionally or because of a bug, the chain keeps making blocks, but they don’t become final.
In 2023, Ethereum stopped finalizing blocks for almost an hour.
This wasn't an attack: it happened because some validator clients had bugs and missed votes.
However, the result was the same as an attack: bridges and exchanges had to stop working because they depend on finality guarantees.
Over-activity. Validators sign conflicting blocks for the same slot, creating forks. Honest validators waste time resolving them. Ethereum counters this with slashing i.e. caught validators lose part of their stake and are ejected.
Bouncing attacks (manipulating fork choice). Validators coordinate to keep switching votes between forks, preventing finality from locking in. The chain appears alive, but no transactions become permanent.
Ordering-Layer Attacks (MEV & Censorship)
These happen not because validators control the chain outright, but because they control transaction ordering inside blocks. Even small sets of validators can extract MEV or censor users to their own profit.
MEV (Maximal Extractable Value). Validators reorder or insert transactions to profit either through front-running (harmful), sandwiching (harmful), back-running (neutral).
Censorship-for-Profit: Validators can exclude or delay transactions to either profit from them or sell the right to include them.
On Ethereum, some builders censor mempool transactions until a private order pays more or until the transactions comply with government regulations.
Why have most of the examples we've discussed so far been from Ethereum?
Why Ethereum is the Gold Standard
Ethereum is the best-studied example of economic security because nearly every type of attack has been theorized, tested, or observed in practice. While not invincible, its design has repeatedly demonstrated resilience, even under real-world stress.
Finality Delays & Reorgs
In May 2023, a client bug caused many validators to go offline, halting finalization for nearly an hour. Ethereum’s inactivity leak kicked in automatically, penalizing idle validators until the system rebalanced.
Blocks kept producing, transactions continued to be processed, and finality was restored — proof that partial outages do not cripple the network.
So far, Ethereum has not experienced a major malicious reorganization (reorg). Because of its PoS finality, reverting confirmed history would require such a large, coordinated effort that it would not be financially worth it.
MEV & Censorship Resistance
While Ethereum offers many MEV opportunities, research into Proposer-Builder Separation (PBS) is underway to prevent centralization. Currently, a few builders create most blocks. However, protocol-level enshrined PBS (ePBS) would distribute this power more evenly to reduce the risk of a few entities gaining too much control.
In late 2022, over half of all blocks were OFAC-compliant, leading to concerns about government influence.
However, new non-censoring relays emerged, causing censorship to drop from 70-80% to around 30-40%.
Even during the peak, censored transactions were only delayed, not permanently blocked, which shows Ethereum's ability to adapt and remain neutral under pressure.
Staking Cartels & Restaking Risks
Liquid staking protocols like Lido highlight the risk of stake concentration by reaching ⅓ of all staked ETH at some times.
Ethereum's security depends on decentralization, which it achieves in several ways:
Encouraging solo stakers
Supporting multiple staking pools
Promoting diverse software clients.
Staking risk is decreasing with the use of Distributed Validator Technology (DVT) protocols like Obol and SSV.
Restaking systems like EigenLayer introduce “coalition risk,” where validator’s stakes are also tied to external protocols. This could expose Ethereum to slashing conditions or incentives beyond its core consensus.
While promising for innovation, it adds new layers of interconnected risk. This also produces the risk of things hard for Ethereum’s consensus by overloading the validators with different tasks.
Inspired by Ethereum and the extensive research around its security, we can now try to make a broader framework to evaluate economic security across different Layer-1 blockchains.
Economic Security Framework
To systematically evaluate the economic security of proof-of-stake and hybrid L1s, we use the following metrics. Each can be qualitatively scored or quantitatively measured depending on available data.
Parameter 1. Security Budget & Expenditure
This is the total yearly amount a chain spends to reward validators for keeping it secure. These rewards come from block subsidies, staking yields, and fees and form the chain’s security budget. A larger budget makes attacks costlier, but also means higher inflation for token holders.
The security budget must strike a balance: too much inflation hurts token holders, too little discourages validator participation. The right level depends on the total value the chain is securing which is a debatable topic.
Parameter 2. Consensus Robustness & Recovery
This category measures how easily a network can be destabilized and how it recovers:
Reorg Thresholds: How Easily validators can reorganize block history.
Finality Delays: How easily attackers or outages can stall transaction finality.
Halt Thresholds: The fraction of validators needed to bring the chain to a full stop.
Recovery & Penalties: Protocol mechanisms for restoring safety (timeout certs, inactivity leaks) and punishing attackers (slashing).
Parameter 3. Validator Decentralization
Security depends on how widely validator power is distributed. Key dimensions:
TVL Distribution Fairness. New metric that measures how evenly staked value and liquidity are spread among validators. A lower score indicates better decentralization.
Geographic & Entity Diversity. Refers to whether validators are concentrated in a single region or controlled by a few large providers.
Client Diversity. Measures the variety and usage share of different software clients used by validators.
Hardware & State Growth. Relates to the technical requirements for running a validator, including hardware specifications and the storage needed to hold the blockchain's history.
Minimum Stake Threshold. Cost required to become a validator.
Parameter 4. Transaction-Level Extraction & Censorship
Beyond chain-wide attacks, economic leakage happens at the transaction layer:
MEV Easiness: This refers to the flexibility validators have to reorder, insert, or steal transactions through methods like front-running, sandwich attacks, or bundle theft.
Censorship Resistance: This measures whether transactions are guaranteed to be included on the blockchain (like in Ethereum's public mempool) or if they risk being permanently dropped (as is the case with some Solana transactions).
Evaluation of Economic Security of Major L1s
We chose to compare the economic security of several major L1 blockchains based on our specific parameters. While this framework can be used to evaluate any L1, our analysis focuses on Ethereum, Solana, Sui, Aptos, and Sei.
Security Budget
In this section, we compare relatively straightforward metrics, such as Total Value Staked and APR, and less obvious one, such as Estimated Annual Security Expenditure, which represents the total rewards paid to validators annually.
Here, the situation is correlative: the lower the total value staked on a chain, the lower its estimated annual security expenditure. Solana can be identified as an outlier in this regard, as the majority of its rewards derive from SOL inflation.
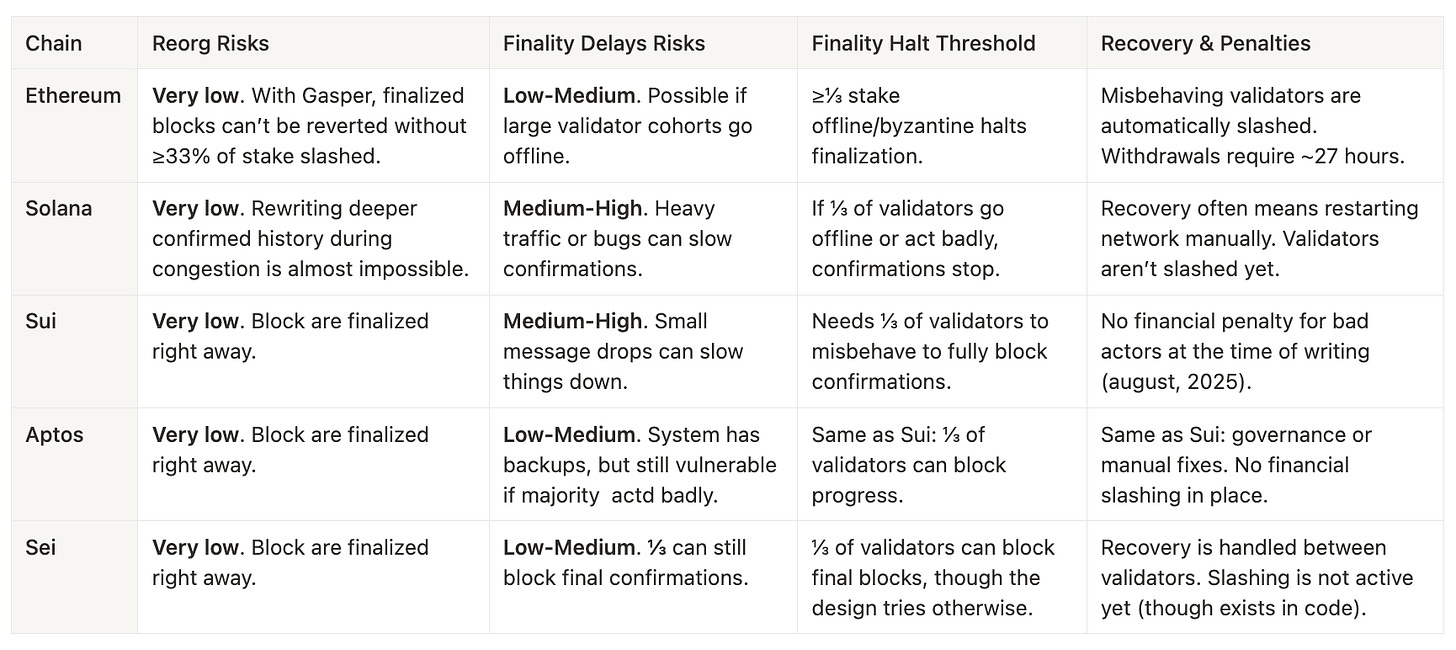
Consensus Robustness & Recovery
In the next section, we measure a variety of parameters related to risks: reorganizations, finality delays, finality halt thresholds, recovery, and penalties.
Reorganization risks are very low across all chains combined, with Sui exhibiting the highest risk of finality delays. Regarding the halt threshold, it is consistent for all Proof-of-Stake (PoS) chains: control of one-third of the total stake can cause issues.
Slashing is currently active only on Ethereum, while on other chains, it is either not implemented or implemented in code (e.g., Sei) but not yet active.
Validator Decentralization Metrics
In this section, we evaluate all aspects related to validators: their global geographic distribution, stake distribution, client diversity, the rate of state growth, and the entry requirements for running a node.
In terms of validator count, Ethereum significantly surpasses all others. However, despite having 1,000 times more validators than Solana, its staked value is only twice as much.
Solana is also the chain with more than two clients, where a single client (Jito) holds over 90% of the stake.
Move-based chains have significantly higher requirements for running a node: $30 million for Sui and $12 million for Aptos, whereas the initial setup cost for an Ethereum node is approximately $118,000.
Solana is the only chain without a minimum staking requirement, but in practice, approximately 5,000 SOL ($900,000) is needed to run competitively. Operating expenses (OPEX) are high due to hardware, bandwidth demands, and voting transactions.
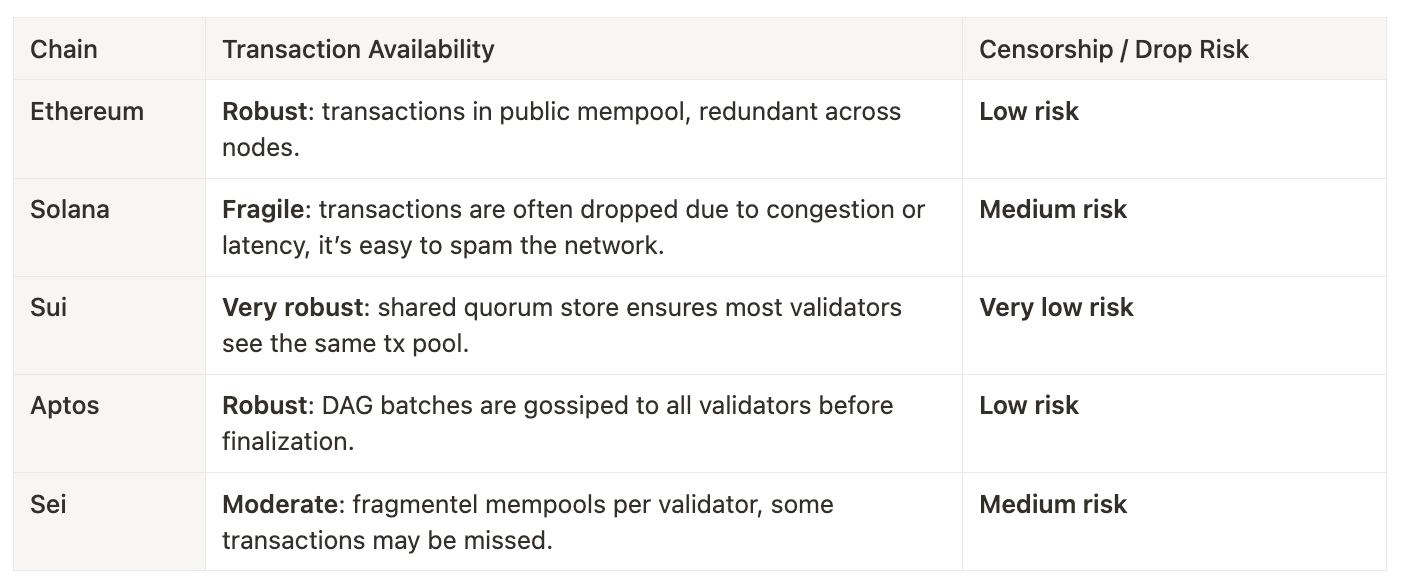
Transaction Level Extraction
We will divide this section into 2 different subsections: MEV and censorship resistance.
DAG-based chains (Sui, Aptos, Sei) eliminate MEV from reorgs, where an attacker reorganizes the chain to capture another validator’s MEV, inherently reducing their MEV ease rating by one star.
In the table below, a higher number of stars indicates greater ease of MEV extraction for the chain.
Censorship resistance focuses on transaction availability and associated risks. Notably, Sui offers the strongest protection against censorship due to its shared quorum store.
Results / Conclusions
Ethereum today remains the benchmark for economic security: expensive to attack, rich in research, and backed by a broad validator base. Its architecture of slashing, inactivity leaks, and client diversity means that attempts to destabilize it are met with high economic and social costs.
When compared to Ethereum, newer chains like Solana, Sui, Aptos, and Sei look like experiments that trade one dimension of security for another. Some maximize throughput, others aim for instant finality, others try to minimize MEV, but in doing so, they narrow their margins of forgiveness.
Where Ethereum offers slow, resilient redundancy, these younger L1s push toward efficiency, speed, or accessibility, often at the cost of deeper centralization risks or fragility under stress.
This contrast highlights a broader fact: economic security is not solely about budgets and slashing but also about time and trust. Ethereum gains time through decentralization and redundancy; alternative L1s prioritize speed with tighter coordination and higher validator thresholds. Both models represent valid experiments, and their success will become evident in the future.
Hazeflow is a blockchain research firm with experience in research, analytics, and the creation of technical, product, and educational materials.
We work with blockchain teams (especially complex-tech ones) who struggle to clearly and meaningfully explain their complex product.